Our ASPM is designed to be your cybersecurity AI Agent, offering continuous support, guidance, and automated solutions to keep your software supply chain secure against evolving threats
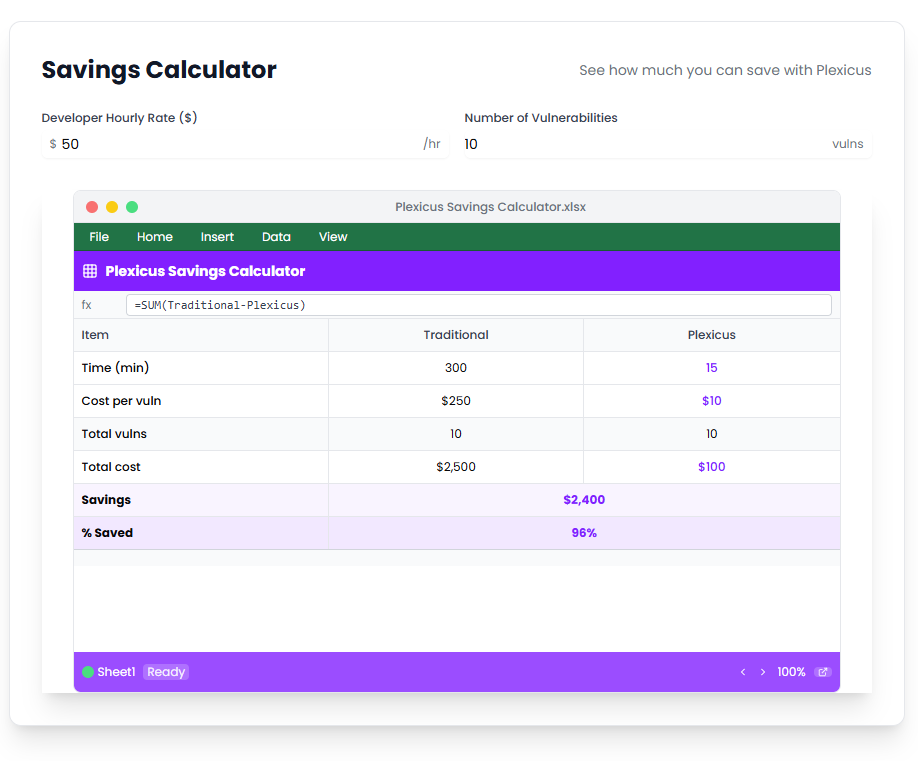
See how Plexicus dramatically accelerates the vulnerability remediation process compared to traditional methods
Plexicus simplifies vulnerability remediation with a three-step process
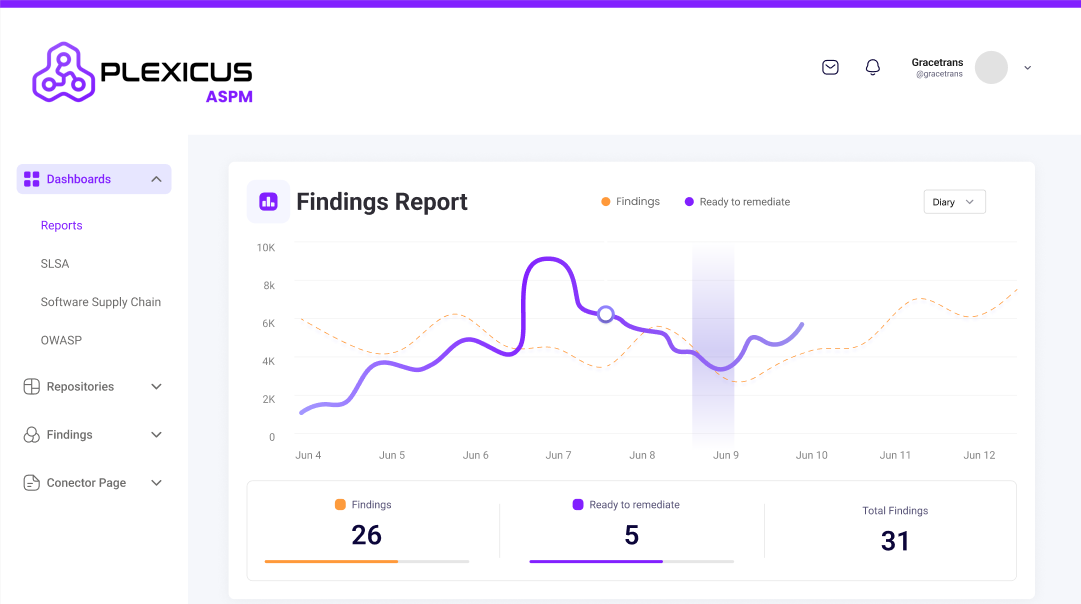
Our advanced scanning technology detects vulnerabilities in your code repositories, identifying security issues like SQL injections before they become threats.
Powered by Plexalyzer
Our scanning technology that continuously monitors your codebase for vulnerabilities
Our advanced scanning technology detects vulnerabilities in your code repositories, identifying security issues like SQL injections before they become threats.
Powered by Plexalyzer
Our scanning technology that continuously monitors your codebase for vulnerabilities
Our advanced scanning technology detects vulnerabilities in your code repositories, identifying security issues like SQL injections before they become threats.
Powered by Plexalyzer
Our scanning technology that continuously monitors your codebase for vulnerabilities
Download our report on how AI-powered ASPM accelerates remediation, reducing response times by 95%
Trusted by leading organizations to secure their software supply chain










Connect Plexicus with your existing tools and workflows
Hear from security teams who have transformed their vulnerability remediation process

“Plexicus has revolutionized our remediation process – our team is saving hours every week!”
CTO, Ontinet

“The integration is seamless, and the AI-powered auto-remediation is a game-changer.”
DevSecOps Lead, Devtia

“We’ve reduced our vulnerability remediation time by 90% since implementing Plexicus.”
Security Engineer, Soluciones 480

“The AI agent’s ability to automatically generate fixes for vulnerabilities has transformed our workflow.”
CTO, Quasar Cybersecurity

“Plexicus has become an essential part of our security toolkit. It’s like having an expert security engineer available 24/7.”
CTO, Quasar Cybersecurity

“Since implementing Plexicus, we’ve seen a dramatic improvement in our security posture with minimal effort from our team. The AI-driven approach to vulnerability remediation is truly revolutionary.”
CTO, Wandari

“Plexicus’s powerful vulnerability management allows us at Puffin Security to deliver more advanced cybersecurity services to our clients, creating a perfect security partnership.”
CEO, Puffin Security

“As pioneers in cloud security, we’ve found Plexicus to be remarkably innovative in the vulnerability remediation space. The fact that they’ve integrated Prowler as one of their connectors demonstrates their commitment to leveraging the best open-source tools while adding significant value through their AI-powered remediation capabilities.”
Founder, Prowler

“As one of Plexicus’s first customers, we’ve witnessed firsthand how their platform has evolved into an indispensable security solution. Their AI-powered remediation has dramatically reduced our vulnerability management overhead and allowed our security team to focus on strategic initiatives instead of repetitive fixes.”
CISO, Ironchip
Elevate your cybersecurity strategy with Plexicus. Contact us for a comprehensive consultation, discover our products through a personalized demo, and learn how Plexicus can fortify your digital infrastructure.
USA 2010 El Camino Real #2456 Santa Clara, CA 95050 USA
EUROPE Madrid International Lab Calle Bailen 41, 28005, Madrid
Mon-Fri 9:00AM - 5:00PM
info@plexicus.com
+1 510-298-1863